Detect the Undetected. Immediately.
Stop wasting weeks to discover breaches. TrapEye's enterprise honeypot platform detects attackers the moment they move, reducing your Mean Time to Detect (MTTD) from months to minutes.
Advanced Cyberattacks Go Undetected for Weeks. Sometimes Years.
Firewalls and EDRs can't detect what's already inside. TrapEye's enterprise honeypot and deception platform closes that blind spot with deceptive security technology.
Why TrapEye
Transform your network into a hostile ground for attackers
MITRE ATT&CK Aligned Detection
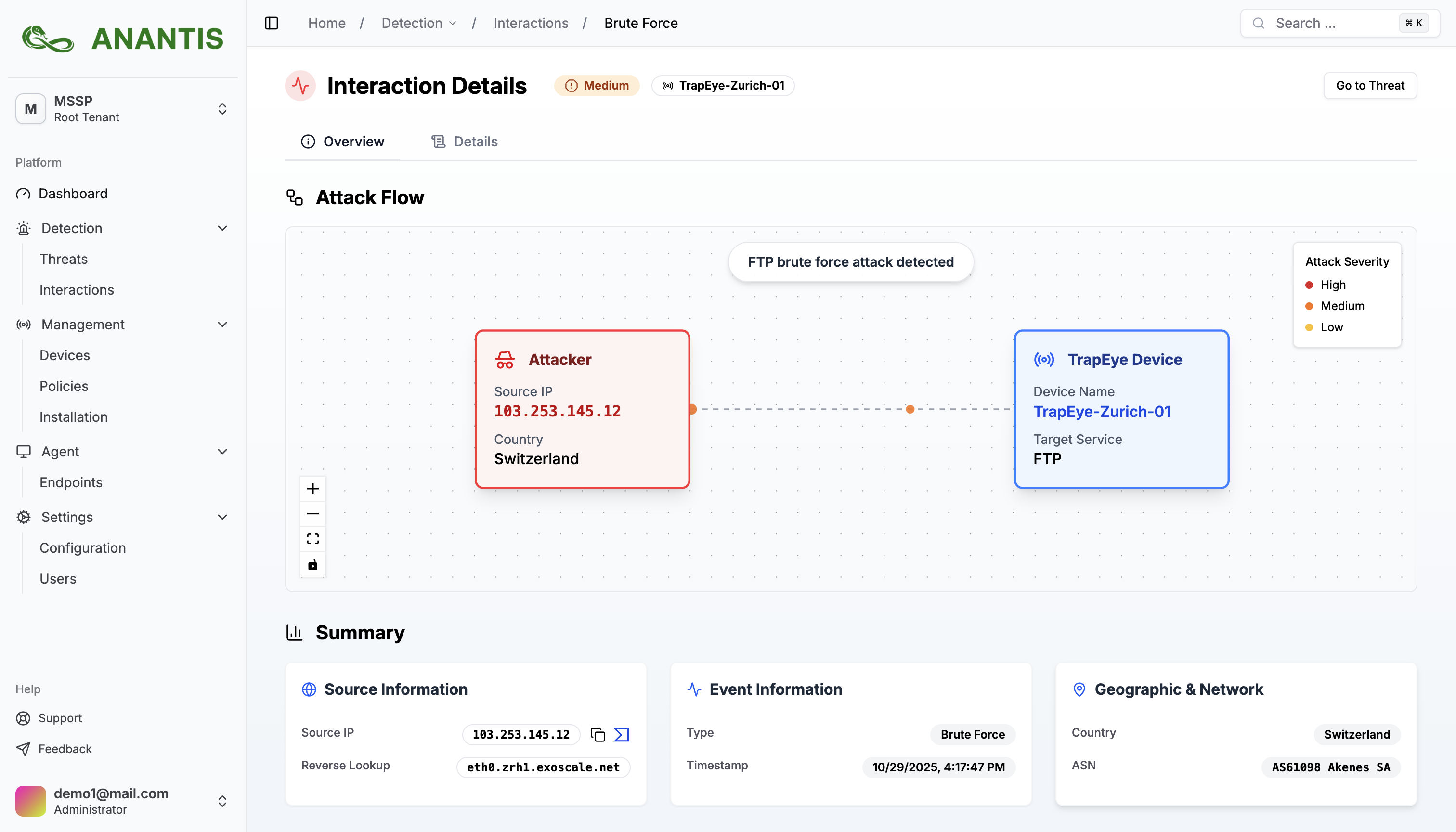
Each detected interaction is automatically mapped to the MITRE ATT&CK framework, giving analysts clear visibility into attacker tactics and techniques.
Reduce MTTD from weeks to minutes
Detect attackers at first touch. Get instant alerts the moment an intruder interacts with a trap - no more blind spots or month-long dwell times.
Full Visibility
See how attackers move inside your network in real-time. Understand their tactics, techniques, and procedures before they cause damage.
High-Fidelity Alerting
Deceptive Security generates only meaningful alerts, no noise, no false positives. Deploy your traps and focus on real threats.
Advanced Analytics & Reporting
Gain clear insights into attacker tactics via interactive dashboards in the web console, complemented by a monthly executive report summarizing activity and risk.
Seamless Integration
Connect with existing SOC workflows and SIEM tools. TrapEye enriches your security stack without disrupting operations.
How TrapEye Works
Deploy Traps. Catch Intruders.
Step 1: Deploy Honeypot Servers
Install TrapEye across your network or cloud infrastructure in seconds. TrapEye's deception engine makes every decoy look authentic and behave like a real server, encouraging attacker interaction.
Step 2: Let Traps Run Silently
TrapEye runs silently in the background. When attackers scan, probe, or attempt logins, they touch a trap and reveal themselves instantly.
Step 3: Get Instant Alerts
When an intruder interacts with any decoy, TrapEye immediately triggers a high-fidelity alert. Receive notifications through Syslog, Webhook, SIEM, or Email with full context on the compromised host and tactic.
Step 4: Contain and Respond
Use the collected intelligence to respond quickly and decisively. Integrate with your SOAR or EDR platform to automate threat containment. Within seconds, your security team gains both visibility and control.
Attackers Exposed Before They Strike.

FAQs
Frequently Asked Questions
Discover how TrapEye's deception platform can fill the gaps in your security stack.
What is TrapEye?
TrapEye is a next-generation enterprise honeypot and deception platform that detects intruders the moment they move inside your network. By deploying realistic traps and decoys, TrapEye provides instant intrusion detection and reduces MTTD from weeks to minutes.
How does TrapEye differ from traditional EDR or SIEM?
Traditional tools focus on prevention and known attack patterns. TrapEye focuses on detection of attackers already inside your network. It complements your existing security stack by filling the blind spots that EDR and SIEM miss.
How long does it take to deploy TrapEye?
TrapEye can be deployed in minutes and appears in your dashboard immediately. It can be installed either on-site using Proxmox, VMware ESXi, Hyper-V, Docker, or in the cloud on AWS and Azure. The setup is streamlined and non-disruptive.
Will TrapEye generate false positives?
No, except in rare cases like authorized penetration tests. Because TrapEye uses deception-based detection, any interaction with a trap is a genuine indicator of malicious activity. Legitimate users and systems never touch honeypots, resulting in virtually zero false positives.
Is TrapEye just a honeypot?
Not quite. While traditional honeypots are useful, they're rarely used internally because managing multiple traps is complex and time-consuming. TrapEye removes these obstacles with a unified console for monitoring and alerts, giving you all the benefits without the technical headaches.
What happens when an attacker triggers a trap?
The moment an attacker interacts with a trap, TrapEye instantly sends an alert with detailed context: what was accessed, when, and from where. Alerts can be delivered to your SOC, SIEM, or directly via email, and you can trigger automated response actions to contain the threat.
Gain Full Visibility into Hidden Threats in Your Network.
Take control of your network protection today.
