· Théo Turletti · For CISO-CIO · 5 min read
OWASP Top 10 2025 - From Exploits to Executive Risks
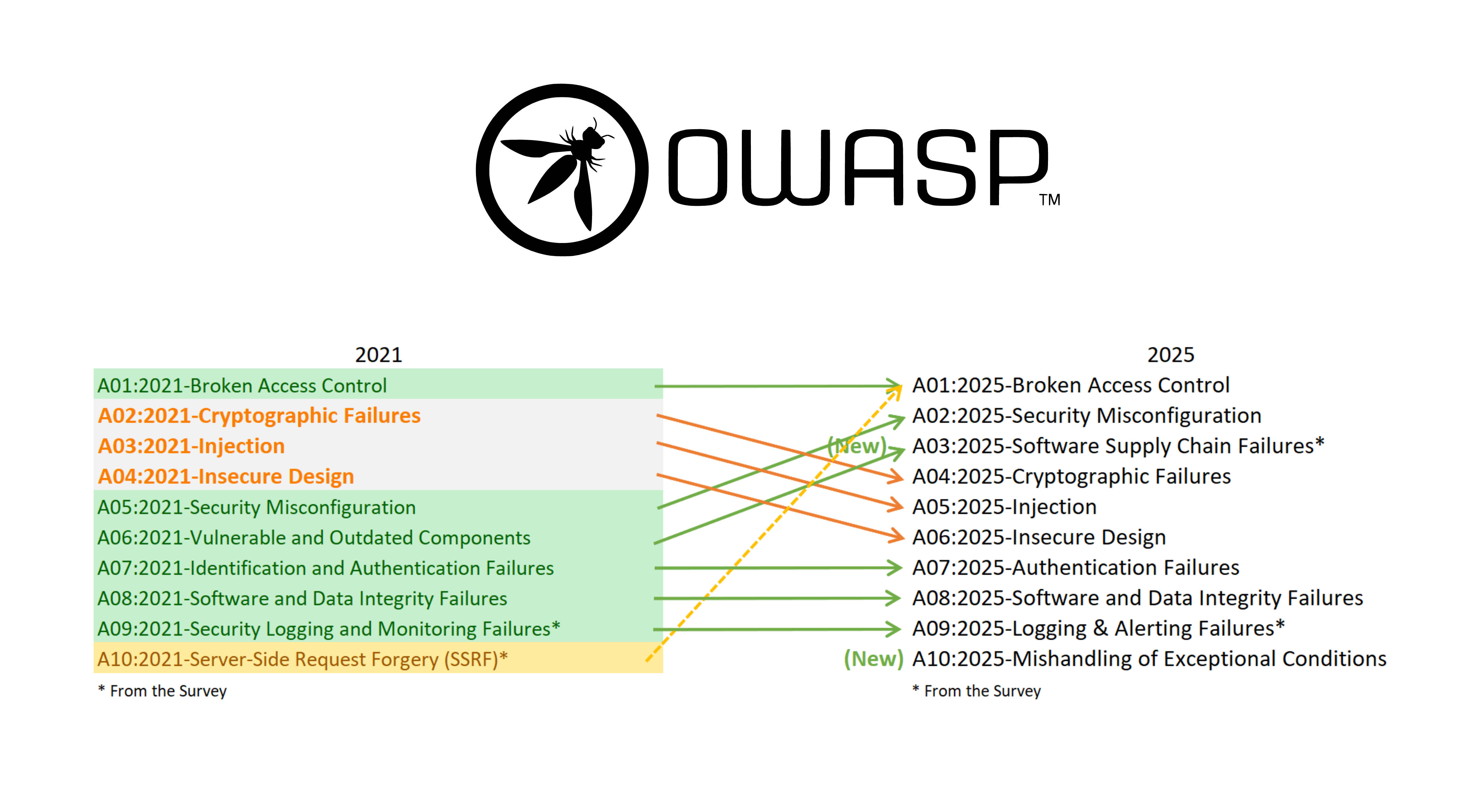
The OWASP Top 10 2025 is out, outlining the most critical security risks facing modern web applications. Two new categories have been added, but the central message remains unchanged: most breaches come from overlooked fundamentals.
OWASP Top 10 2025 – From Exploits to Executive Risks
The OWASP Top 10 is a long-standing industry benchmark maintained by the Open Worldwide Application Security Project, a non-profit organization dedicated to improving software security globally. Far from being a compliance checklist, it serves as a data-driven awareness framework, summarizing the most common and impactful risks observed across real-world applications and security assessments.
For CISOs and security leaders, the Top 10 is a strategic reference: it highlights where modern development and DevSecOps programs typically fail, and where to focus resources for the highest risk reduction.
The 2025 Release Candidate (RC) reflects today’s evolving threat landscape - with new emphasis on software supply chain integrity and secure design - while reinforcing a familiar truth: even in 2025, most compromises still come from simple, preventable weaknesses.
This guide provides a clear, field-oriented view of each category, with concise examples, minimal proof-of-concepts (POCs), and actionable remediation steps to help bridge the gap between theory and implementation.
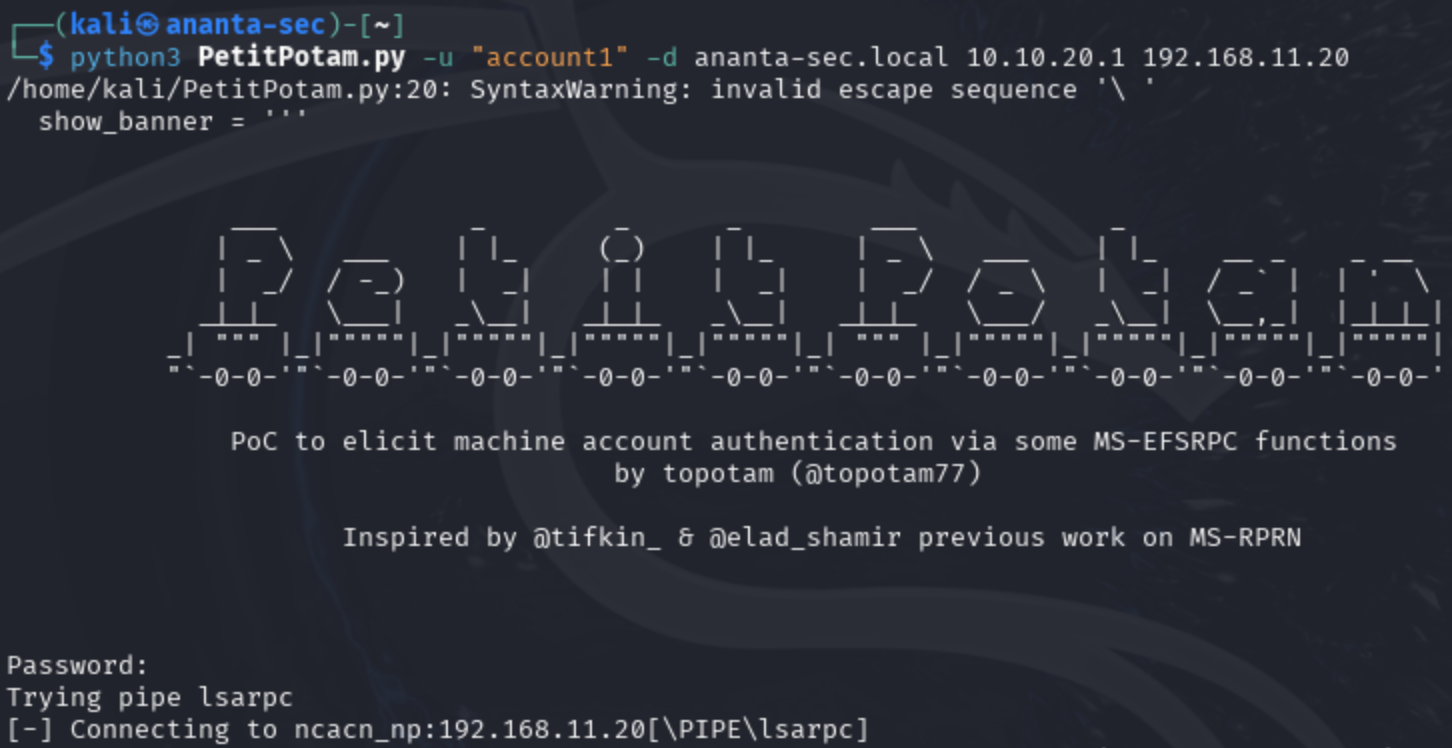
A01:2025 – Broken Access Control
Why it matters: Unauthorized access remains the #1 risk for web applications. It creates immediate business risk: leaked customer data, regulatory fines, and rapid erosion of trust once attackers move laterally with elevated privileges.
Example: A user accessing another tenant’s data by modifying an ID in the URL.
POC
GET /api/v1/users/1234 → valid responseGET /api/v1/users/1235 → if this returns data for another user, access control is brokenRemediation: Enforce server-side authorization for every request. Check session, ownership and ACLs on the server, never trust client input for authorization.
A02:2025 – Security Misconfiguration
Why it matters: Every component from cloud services to frameworks can introduce exposure if security defaults aren’t hardened. These simple mistakes are a common, high‑impact entry vector for attackers.
Example: A production S3 bucket left publicly readable.
POC
# List publicly accessible S3 bucketsaws s3 ls s3://example-bucket --no-sign-requestRemediation: Establish a baseline hardening checklist for servers, containers, and cloud services. Disable unused ports and features, enforce least privilege and continuously audit configurations through automated scanning and IaC validation.
A03:2025 – Software Supply Chain Failures
Why it matters: Compromised dependencies or build pipelines can affect many applications at once.
Example: A vulnerable or compromised package being installed and used in your application.
POC
# A malicious NPM package published to a widely used package name.npm install vuln-package@1.0.0Remediation: There should be a patch management process in place to track not just your own dependencies, but their (transitive) dependencies. Remove unused dependencies, unnecessary features, components, files, and documentation. Continuously monitor sources like Common Vulnerability and Exposures (CVE) for vulnerabilities in the components you use.
A04:2025 – Cryptographic Failures
Why it matters: Weak or misused crypto leads to data exposure and impersonation.
Example: Storing passwords with plain SHA‑256, without salt, pepper, or a proper key-derivation function.
POC
# Export the hashes and run an offline cracker or rainbow-table lookuphashcat -m 1400 hashes.txt /path/rockyou.txt --showRemediation: Use modern, memory-hard password hashing like Argon2id with proper salt and pepper.
A05:2025 – Injection
Why it matters: Injection flaws let attackers run unintended commands or queries.
Example: SQL injection in a search input.
POC
Input: '; DROP TABLE users;--If the app executes it and errors or data disappears, injection existsRemediation: Use parameterized queries / prepared statements or safe ORM APIs, validate and sanitize inputs, apply least privilege to DB accounts.
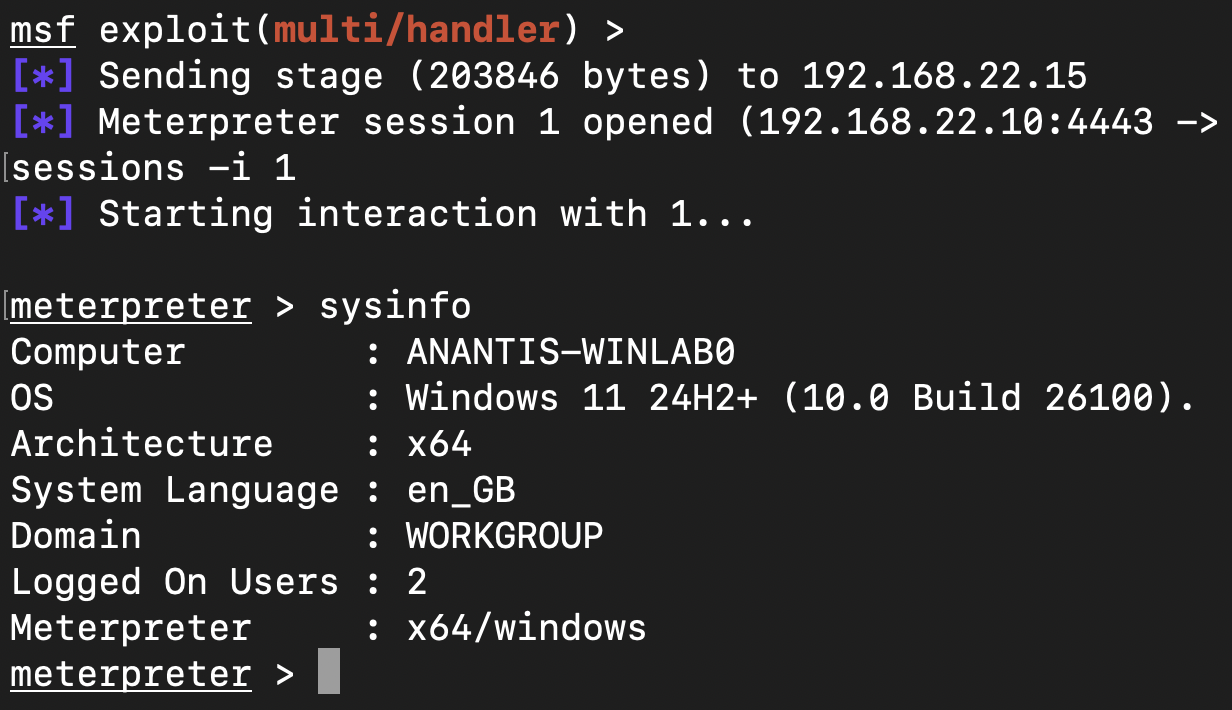
A06:2025 – Insecure Design
Why it matters: Design-level flaws create broad, systemic weaknesses that are hard to patch later.
Example: An API blindly trusts client-controlled fields (e.g., is_admin in JSON or a X-User-Role header) and uses them to make authorization decisions, enabling privilege escalation or unauthorized business actions.
POC
curl -sS -X POST http://localhost:3001/api/transfer \ -H "Authorization: Bearer attacker" \ -H "Content-Type: application/json" \ -d '{"from":"alice","to":"bob","amount":1000,"is_admin":true}'
# Server responds 200 OK and performs privileged action because it trusted is_admin in client request bodyRemediation: Never trust client-controlled fields for decisions that require authority. Server side must be authoritative for roles/permissions. Adopt secure-by-design patterns and bake security reviews into development lifecycle.
A07:2025 – Authentication Failures
Why it matters: Weak authentication allows impersonation and privilege escalation.
Example: Weak password policy, predictable session tokens, or token reuse.
POC
Brute-force common passwords against login or replay a captured token to access an accountRemediation: Enforce MFA, strong password policy, rate limiting, token rotation, and secure session handling.
A08:2025 – Software or Data Integrity Failures
Why it matters: Tampered binaries, packages, or data can run malicious logic without immediate detection.
Example: Modified config or binary deployed to production.
POC
Replace a binary or config in a test environment and verify the app loads/executes itRemediation: Use signed artifacts (checksums, digital signatures), verify signatures at deploy/runtime, and protect build artifacts and deployment channels.
A09:2025 – Logging & Alerting Failures
Why it matters: If you can’t detect or alert on malicious activity, compromise persists longer.
Example: Critical admin actions produce no logs or alerts.
POC
Perform admin action and search logs. If nothing is recorded or no alert is triggered, detection failsRemediation: Ensure comprehensive logging of security-relevant events, pipeline logs to a tamper-resistant system, create actionable alerts, and regularly test detection processes.
A10:2025 – Mishandling of Exceptional Conditions
Why it matters: Poor error handling can leak secrets or leave systems in unsafe states.
Example: Stack traces returned to users revealing internals or failing-open on error.
POC
Submit malformed input to trigger an exception; check for stack traces or sensitive data in the responseRemediation: Handle errors gracefully, fail securely (deny by default), sanitize error messages, and log detailed internals only to protected logs.
Conclusion
The OWASP Top 10 2025 reinforces a simple truth: fix the basics first. Most breaches don’t stem from niche “GenAI exploits” but from common, preventable mistakes.
Organizations must ensure the fundamentals are mastered: strong access control, secure configurations, dependency governance, and safe input handling.
For CISOs, the message is clear: these technical flaws translate directly into business risks - data exposure, service disruption, reputational damage, and regulatory non-compliance.
At Anantis, our mission is to bridge the gap between exploitation and executive risk.
We identify critical weaknesses, prioritize fixes by business impact, and deliver pragmatic, verifiable remediation so you can reduce exposure quickly and measurably.