· Threat Hunting Team · Anantis Security Labs · 4 min read
Unpatched Windows flaw lets attackers disable AV/EDR and deploy ransomware
Researchers uncovered a Windows design flaw that lets attackers pause protected security processes via WerFaultSecure.exe, leaving organizations exposed until Microsoft releases a fix.
Modern Windows endpoint protection relies on a layered approach: kernel-level telemetry, Protected Process Light (PPL) processes, signed binaries and deep behaviour monitoring. Those layers dramatically increase the cost of successful attacks, but they are not an absolute guarantee. In this article we demonstrate a novel, practical technique that leverages a legitimate OS helper — WerFaultSecure.exe (the Windows Error Reporting secure helper) — to temporarily neutralize high-integrity security processes.
Why This Vulnerability Matters
Defenders typically focus on preventing initial compromise or on detecting and responding to malicious activity once it occurs. This flaw creates a dangerous blind spot between initial compromise and detection by directly disabling the very processes responsible for monitoring and response.
From an incident-response perspective, the impact is severe: an attacker with code execution can effectively neutralize security solutions and operate without resistance. That freedom enables attackers to exfiltrate sensitive data, deploy ransomware, move laterally across the network, and establish long-term persistence — all before defenders can observe or respond.
Hijacking WerFaultSecure’s Resume Operation
WerFaultSecure.exe is a legitimate Windows Error Reporting helper responsible for producing crash dumps for both ordinary and protected processes. Unlike normal processes, it is signed with a special certificate that includes the WinTCB Extended Key Usage (EKU). This EKU gives it the rare privilege to access and tamper with any Protected Process Light (PPL) binaries — such as antivirus and EDR agents.
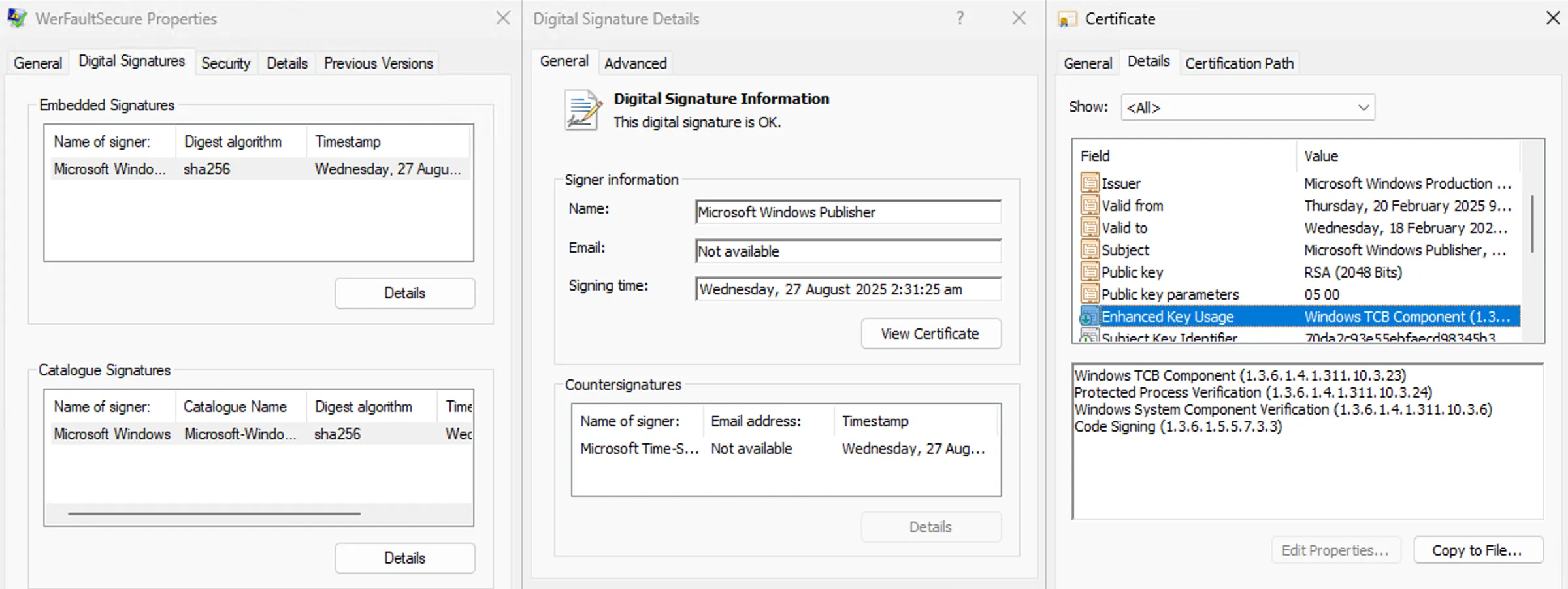
When creating a crash dump, WerFaultSecure.exe briefly suspends the target process, captures its memory and state, and then resumes it. This brief suspension is legitimate and expected behavior.
The vulnerability arises because this sequence creates a short, observable window during which the protected process is suspended, introducing a classic race condition. An attacker who monitors that window can interfere with the crash helper as it attempts to resume the target process. By preventing the helper from resuming the process, the attacker can keep the protected process suspended — effectively halting the defensive component for as long as needed.
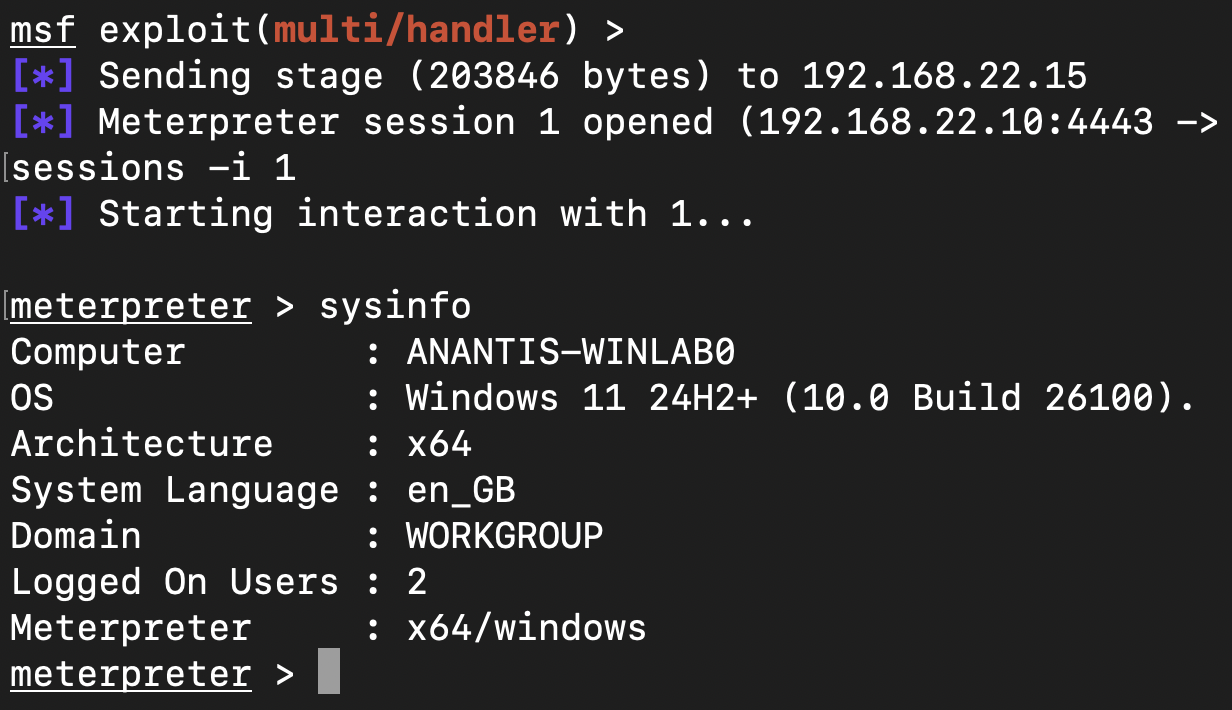
Demonstrating the Exploit
The Anantis Security Team developed a proof-of-concept (PoC) to validate this technique - StopEDR. Using it, we successfully executed a well-known offensive payload — a Meterpreter reverse shell — on the latest Windows 11 with Microsoft Defender enabled. Despite being a payload flagged for more than a decade, the PoC allowed it to run, granting full attacker-level access to the system: data exfiltration, ransomware deployment, or any arbitrary action.
StopEDR — open-source PoC (GitHub): https://github.com/anantis-security/stop-edr
How to Test Your Endpoint Protection
Organizations can use this PoC to verify if their endpoint protection is vulnerable and to confirm that their SIEM can detect the activity. Administrators can additionally check if their antivirus or EDR is being suspended by monitoring processes with tools like Process Explorer from the Sysinternals Suite.
⚠️ Important: the PoC is unstable and may cause system crashes. Testing must only be performed in isolated environments such as non-production machines or dedicated virtual machines.
Our security team is available for free short calls to assist with running these checks and configuring your EDR or SIEM for proper visibility. You can reach us at contact@anantis.io or via our contact form.
Mitigation and Detection Guidance
Microsoft has not yet released an official remediation. Until a patch is available, organizations should implement custom detection and response rules in their EDR and SIEM solutions to identify and block suspicious use of WerFaultSecure.exe.
Anantis has developed a Sigma rule that can be imported into modern detection platforms.
title: Suspicious Process Access to WerFaultSecure.exeid: 7b2e8f1a-4c9d-3e6f-8a5b-1d7c9eef2a8bstatus: experimentaldescription: Detects suspicious process access to WerFaultSecure.exe indicating potential StopEDR attackauthor: Anantisdate: 02.10.2025references: - https://github.com/anantis-security/mute-edrtags: - attack.defense_evasion - attack.t1562logsource: category: process_access product: windowsdetection: selection_target: TargetImage|endswith: '\WerFaultSecure.exe' GrantedAccess: - '0x1000' # PROCESS_SUSPEND_RESUME - '0x1400' # PROCESS_SUSPEND_RESUME | PROCESS_QUERY_INFORMATION - '0x1F0FFF' # PROCESS_ALL_ACCESS filter_legitimate: SourceImage|startswith: - 'C:\Windows\System32\' - 'C:\Windows\SysWOW64\' SourceImage|endswith: - '\svchost.exe' - '\services.exe' - '\winlogon.exe' condition: selection_target and not filter_legitimatefalsepositives: - Debugging tools used by administratorslevel: highWe believe this will help security teams stay ahead of the threat by flagging anomalous activity involving the vulnerable helper process before attackers can exploit it.
Credits
Original research and technique discovery: TwoSevenOneT